A beforehand unknown piece of ransomware, dubbed ShrinkLocker, encrypts sufferer information utilizing the BitLocker characteristic constructed into the Home windows working system.
BitLocker is a full-volume encryptor that debuted in 2007 with the discharge of Home windows Vista. Customers make use of it to encrypt whole laborious drives to stop folks from studying or modifying information within the occasion they get bodily entry to the disk. Beginning with the rollout of Home windows 10, BitLocker by default has used the 128-bit and 256-bit XTS-AES encryption algorithm, giving the characteristic further safety from assaults that depend on manipulating cipher textual content to trigger predictable adjustments in plain textual content.
Not too long ago, researchers from safety agency Kaspersky discovered a risk actor utilizing BitLocker to encrypt information on techniques situated in Mexico, Indonesia, and Jordan. The researchers named the brand new ransomware ShrinkLocker, each for its use of BitLocker and since it shrinks the scale of every non-boot partition by 100 MB and splits the newly unallocated area into new main partitions of the identical dimension.
“Our incident response and malware evaluation are proof that attackers are consistently refining their techniques to evade detection,” the researchers wrote Friday. “On this incident, we noticed the abuse of the native BitLocker characteristic for unauthorized information encryption.”
ShrinkLocker isn’t the primary malware to leverage BitLocker. In 2022, Microsoft reported that ransomware attackers with a nexus to Iran additionally used the device to encrypt recordsdata. That very same yr, the Russian agricultural enterprise Miratorg was attacked by ransomware that used BitLocker to encrypt recordsdata residing within the system storage of contaminated units.
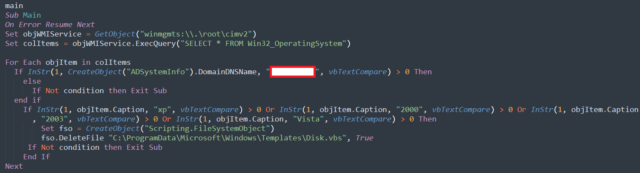
As soon as put in on a tool, ShrinkLocker runs a VisualBasic script that first invokes the Home windows Administration Instrumentation and Win32_OperatingSystem class to acquire details about the working system.
“For every object throughout the question outcomes, the script checks if the present area is completely different from the goal,” the Kaspersky researchers wrote. “Whether it is, the script finishes routinely. After that, it checks if the identify of the working system incorporates ‘xp,’ ‘2000,’ ‘2003,’ or ‘vista,’ and if the Home windows model matches any considered one of these, the script finishes routinely and deletes itself.”
Kaspersky
The script then continues to make use of the WMI for querying details about the OS. It goes on to carry out the disk resizing operations, which may differ relying on the OS model detected. The ransomware performs these operations solely on native, fastened drives. The choice to go away community drives alone is probably going motivated by the will to not set off community detection protections.
Commercial
Ultimately, ShrinkLocker disables protections designed to safe the BitLocker encryption key and goes on to delete them. It then allows the usage of a numerical password, each as a protector in opposition to anybody else taking again management of BitLocker and as an encryptor for system information. The explanation for deleting the default protectors is to disable key restoration options by the system proprietor. ShrinkLocker then goes on to generate a 64-character encryption key utilizing random multiplication and substitute of:
A variable with the numbers 0–9;
The well-known pangram, “The short brown fox jumps over the lazy canine,” in lowercase and uppercase, which incorporates each letter of the English alphabet;
Particular characters.
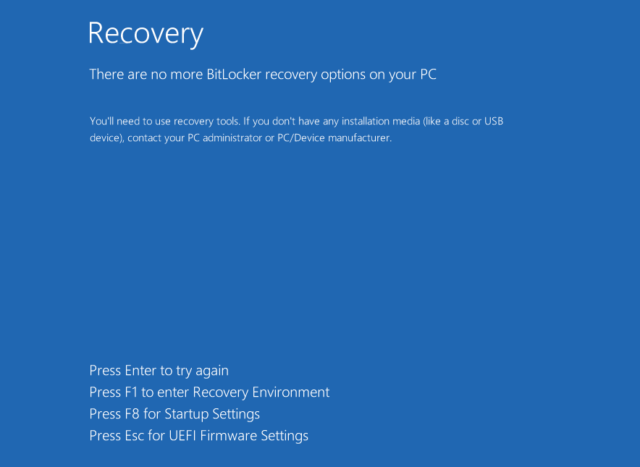
After a number of extra steps, information is encrypted. The following time the system reboots, the show appears like this:
Kaspersky
Decrypting drives with out the attacker-supplied secret is troublesome and certain unattainable in lots of instances. Whereas it’s attainable to get well a number of the passphrases and glued values used to generate the keys, the script makes use of variable values which are completely different on every contaminated system. These variable values aren’t straightforward to get well.
There are not any protections particular to ShrinkLocker for stopping profitable assaults. Kaspersky advises the next:
Use strong, correctly configured endpoint safety to detect threats that attempt to abuse BitLocker;
Implement Managed Detection and Response (MDR) to proactively scan for threats;
If BitLocker is enabled, be certain it makes use of a robust password and that the restoration keys are saved in a safe location;
Make sure that customers have solely minimal privileges. This prevents them from enabling encryption options or altering registry keys on their very own;
Allow community visitors logging and monitoring. Configure the logging of each GET and POST requests. In case of an infection, the requests made to the attacker’s area might include passwords or keys;
Monitor for occasions related to VBS execution and PowerShell, then save the logged scripts and instructions to an exterior repository storing exercise which may be deleted regionally;
Make backups continuously, retailer them offline, and take a look at them.
Friday’s report additionally consists of indicators that organizations can use to find out if they’ve been focused by ShrinkLocker.






















