A infamous North Korean hacking group has been accused of stealing delicate info and blueprints about weapons, torpedoes and different weapon techniques.
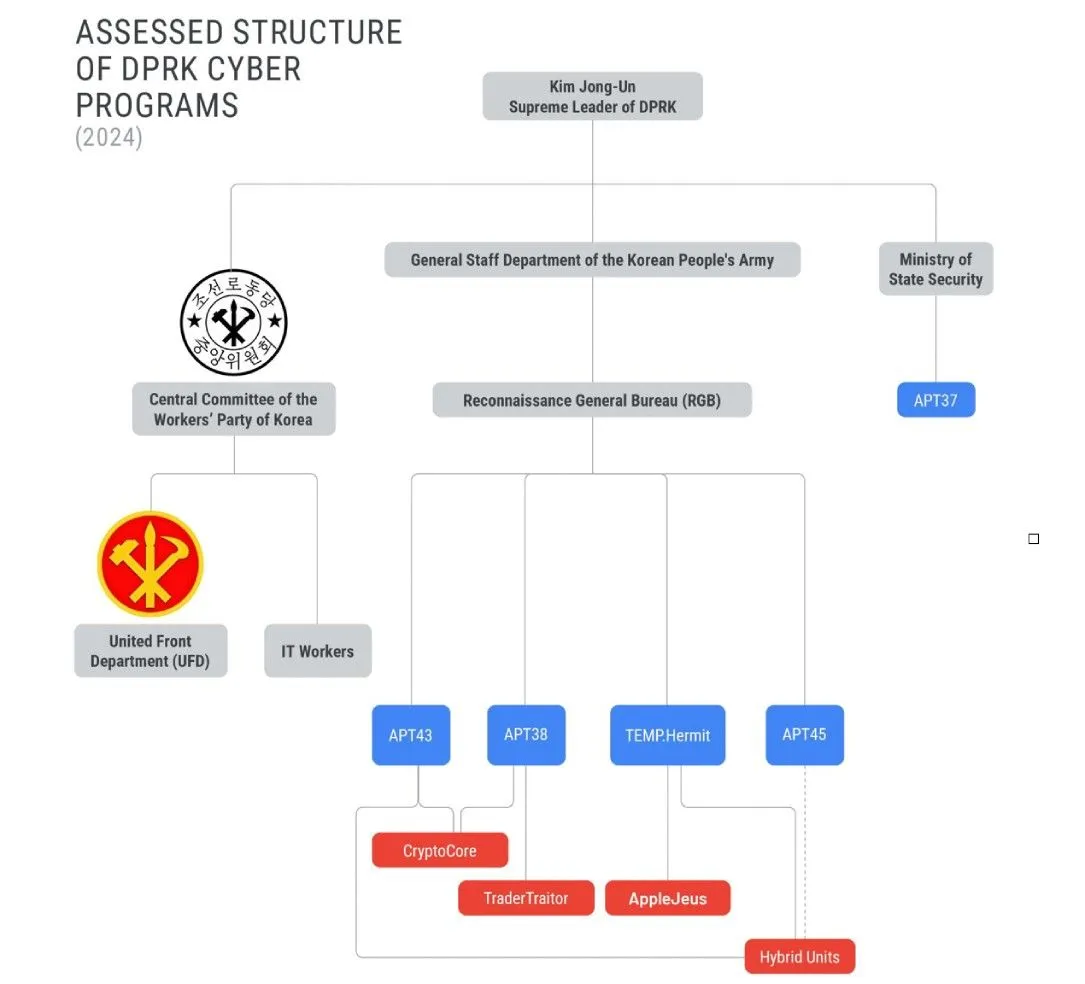
Cybersecurity agency Mandiant revealed on Thursday the outcomes of a two-year investigation into Andariel — a widely known group of hackers U.S. officers imagine is tied to North Korea’s intelligence workplace, the Reconnaissance Basic Bureau.
Researchers mentioned Andariel has launched a number of massive, impactful cyber operations that focused crucial infrastructure — increasing past authorities espionage campaigns into ransomware assaults on hospitals, banks and South Korean protection corporations.
Michael Barnhart, who leads Mandiant’s North Korean threat-hunting crew, instructed Recorded Future Information that many advances in North Korea’s navy capabilities lately can immediately be attributed to the group’s profitable espionage efforts towards governments and protection organizations world wide. As a result of group’s rising sophistication, Mandiant mentioned it was giving Andariel a sophisticated persistent risk (APT) tag of APT45.
“When Kim Jong Un calls for higher missiles, these are the blokes who steal the blueprints for him. APT45 isn’t sure by moral issues and have demonstrated they’re keen and agile sufficient to focus on any entity to realize their targets, together with hospitals,” Barnhart mentioned.
Picture: Mandiant
“A coordinated international effort involving each private and non-private sectors is important to counter this persistent and evolving risk.”
Mandiant mentioned it labored alongside the FBI and different authorities businesses to trace the group’s assaults on healthcare suppliers, protection contractors and authorities nuclear services world wide.
Mandiant mentioned consultants and authorities businesses have been alarmed by APT45’s potential to steal delicate plans a few vary of weapons and instruments together with:
Heavy and light-weight tanks and self-propelled howitzersLight strike autos and ammunition provide vehiclesLittoral fight ships and combatant craftSubmarines, torpedoes, unmanned underwater autos (UUV), and autonomous underwater autos (AUV)Modeling and simulation servicesFighter plane and unmanned aerial autos (UAV)Missiles and missile protection systemsSatellites, satellite tv for pc communications, and nano-satellite technologySurveillance radar, phased-array radar, and different radar systemsUranium processing and enrichmentMaterial waste and storageNuclear energy plantsGovernment nuclear services and analysis institutesShipbuilding and marine engineeringRobot equipment and mechanical armsAdditive manufacturing and 3D printing parts and technologyCasting, fabrication, high-heat metallic molding, and rubber and plastic moldingMachining processes and expertise
Mandiant mentioned the group’s espionage campaigns date again to 2009 and it has progressively expanded into financially-motivated assaults — its use of ransomware separates it from different North Korean operators. Some strains of malware utilized by the group are distinct from the toolset utilized by different teams within the nation.
In 2019, the group focused Kudankulam Nuclear Energy Plant in India, Mandiant mentioned, including that different nuclear services and energy vegetation have been focused. The group additionally went after the crop science division of a multinational company in 2020 and several other healthcare and pharmaceutical verticals over the past 4 years.
Picture: Mandiant
“APT45 is certainly one of North Korea’s longest working cyber operators, and the group’s exercise mirrors the regime’s geopolitical priorities at the same time as operations have shifted from basic cyber espionage towards authorities and protection entities to incorporate healthcare and crop science,” the researchers mentioned.
“Financially motivated exercise occurring alongside intelligence assortment has turn into a defining attribute of North Korean cyber operations, and we anticipate APT45 to proceed each missions. Because the nation has turn into reliant on its cyber operations as an instrument of nationwide energy, the operations carried out by APT45 and different North Korean cyber operators could mirror the altering priorities of the nation’s management.”
The report notes that the group has been tied to the Lazarus Group — one other North Korean operation that has performed dozens of hacks on monetary establishments.
In December, the Seoul Metropolitan Police accused APT45 of stealing delicate details about anti-aircraft weapon techniques from South Korean corporations. South Korea’s authorities warned in April that the group spent most of 2022 and 2023 infiltrating the networks of 83 South Korean protection corporations or their contractors.
The group was sanctioned in 2019 by the U.S. Treasury, which mentioned the group “constantly executes cybercrime to generate income and targets South Korea’s authorities and infrastructure with the intention to acquire info and to create dysfunction.”
Recorded Future
Intelligence Cloud.
Study extra.






















