14 Feb Empowering SOC Groups with Open and Seamless API Integration
in Blogs
Boosting SOC Effectivity with Open XDR and API Integration
– Peter Luo, Director of Product Administration, Stellar Cyber
San Jose, Calif. – Feb. 14, 2025
In the present day’s complicated cyber risk panorama poses each enterprises and Managed Safety Service Suppliers (MSSPs) a number of challenges. To fight advanced threats throughout various IT & safety environments, cybersecurity professionals develop an array of instruments and knowledge sources to watch their particular risk panorama. Nonetheless, the software array presents its personal difficulties, as there are gaps in visibility, excessive calls for of small analyst groups, and redundancies in performance. The next weblog will discover methods in which you’ll improve your safety operations with out creating extra burden to your analyst group.
Why Openness Issues for SOC Groups
No single cybersecurity software is infallible. SOC analysts and MSSPs depend on a various set of options to watch, detect, and reply to threats. Reasonably than contribute an extra redundant software, Stellar Cyber’s Open XDR platform:
Integrates seamlessly together with your present safety stack.
Helps a number of knowledge ingestion strategies to accommodate various environments.
Permits customization to satisfy distinctive operational wants of every SOC group.
At Stellar Cyber, we don’t consider in locking you right into a proprietary ecosystem. As an alternative, we offer the instruments and suppleness to adapt to your atmosphere, making certain you may leverage the perfect options in your wants.
The Position of APIs in Fashionable SOC Groups
An API (Utility Programming Interface) is a set of protocols and instruments that allow completely different software program purposes to speak with one another. APIs function the glue that binds your safety ecosystem collectively, facilitating knowledge sharing, automation, and orchestration. They’re the spine of recent cybersecurity, enabling programs to speak, share knowledge, and execute actions programmatically.
APIs are deeply embedded in each side of recent SOC operations, usually working behind the scenes to make sure seamless collaboration between instruments and groups.
“Inside Brite’s Safety Operations Middle (SOC), API logging is crucial for steady safety monitoring and incident response, enabling organizations to successfully defend towards incidents probably resulting in a breach,” says Jon-Michael Lacek, CTO at Brite. “Over time, API logging has transitioned from a basic software to a vital factor of cybersecurity protection. With the continuing shift towards SaaS and cloud-based options, the power to entry and analyze safety logs from purposes is more and more crucial. Moreover, the capability to leverage APIs for real-time response actions—akin to mitigating threats—is a key space the place Brite’s analysts information clients to reinforce playbook maturity, considerably lowering the potential for lateral motion by malicious actors throughout the community.”
Challenges of Integration
Regardless of their vital function, reaching seamless API integration isn’t any simple activity. Frequent challenges embody:
Totally different Protocols/Syntax: Variability in API requirements, akin to REST, GraphQL, or SOAP, or fully proprietary
Totally different Parameters/Semantics: Lack of uniformity in how knowledge is structured, outlined or handed.
Authentication Mechanisms: Numerous strategies like OAuth, API keys, or token-based authentication.
Inconsistent Practices: Many distributors don’t adhere to constant or clear API practices, making integrations cumbersome.
Stellar Cyber addresses these challenges by simplifying the mixing course of and making certain compatibility throughout various applied sciences.
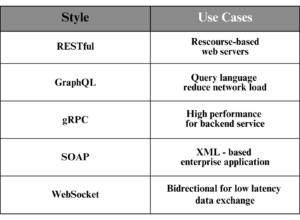
Selection sorts of API Protocols and Specs
In apply, There are a number of sorts of APIs, every designed for particular use circumstances:
RESTful API: A light-weight, widely-used protocol for net companies.
GraphQL: A question language that permits purchasers to request precisely the info they want, lowering community latency.
gRPC: A high-performance protocol for microservices, utilizing Protocol Buffers for knowledge serialization.
SOAP: A legacy protocol for structured info trade, usually utilized in enterprise programs.
WebSocket: A protocol for real-time, bidirectional communication, best for low-latency purposes.
Whereas RESTful APIs are the commonest in safety software integrations, some instruments additionally use GraphQL or different protocols.
Selection sorts of API Authentication Mechanisms
Totally different distributors use varied authentication strategies to make sure safe communication. Frequent mechanisms embody:
OAuth 2.0: The trade customary for authorization, permitting safe entry to sources.
Primary Authentication: A easy methodology utilizing a username and password, usually encoded in Base64.
Token Authentication: Makes use of tokens (e.g., JWTs) to confirm identification and permissions.
API Key Authentication: A simple methodology the place a novel key’s used to authenticate requests.
Entry Key/Secret Key: A pair of keys used for authentication and authorization.
Selection sorts of API Requirements: The Basis of Interoperability
API requirements guarantee consistency, interoperability, and ease of use. There are a selection of API requirements over time. The OpenAPI Specification (OAS), previously often known as Swagger, is probably the most broadly adopted customary for outlining RESTful APIs. Nonetheless, there are options, akin to:
RAML: A YAML-based language for describing RESTful APIs.
API Blueprint: A Markdown-based language for API documentation.
Inconsistent high quality of APIs amongst completely different distributors
The standard of APIs can fluctuate considerably throughout distributors, creating challenges for seamless integration and interoperability. A well-designed API is vital for making certain easy communication between programs and lowering the burden on SOC groups. Key traits of a high-quality API embody:
Correct Versioning: Ensures backward compatibility, permitting programs to evolve with out breaking present integrations.
Clear Documentation: Offers easy-to-understand tips, examples, and use circumstances, enabling builders to implement integrations shortly and precisely.
Sturdy Error Dealing with: Delivers significant error codes and messages to assist diagnose and resolve points effectively.
Throttling and Limits: Prevents abuse and ensures system stability by controlling the speed of API requests.
Clear, Nested Outcomes: Buildings knowledge in a logical, easy-to-parse format, lowering the complexity of processing and evaluation.
Sadly, not all distributors adhere to those finest practices, resulting in inconsistent API high quality. Poorly designed APIs can lead to integration complications, elevated growth time, and operational inefficiencies.
APIs: The Basis for Innovation
As we enter the period of AI-driven SOCs, APIs are extra vital than ever. Whether or not it’s for automation, Gen AI, or AI-based SOC operations, APIs are the basic elements that allow innovation. At Stellar Cyber, we’re embracing this integration-driven future, making it simpler so that you can automate, orchestrate, and collaborate throughout your safety ecosystem. With APIs on the core of our platform, we’re empowering SOC groups to shortly remediate dangers, streamline workflows, and keep forward of evolving threats.
Conclusion
In a world the place cybersecurity threats are always evolving, cybersecurity analysts must undertake probably the most strategic and environment friendly answer to fight any sort of risk at any level of their IT & safety panorama. An open and versatile XDR platform is not a luxurious—it’s a necessity. Stellar Cyber’s Open XDR Platform, powered by a sturdy API basis, empowers SOC analysts and MSSPs to combine, innovate, and reply with confidence.
Able to expertise the ability of seamless integration? Contact us immediately to study extra about how Stellar Cyber can remodel your safety operations.
– Peter Luo is the Director of Product Administration at Stellar Cyber.

Stellar Cyber’s Open XDR Platform delivers complete, unified safety with out complexity, empowering lean safety groups of any talent degree to safe their environments efficiently. With Stellar Cyber, organizations scale back threat with early and exact identification and remediation of threats whereas slashing prices, retaining investments in present instruments, and enhancing analyst productiveness, delivering an 8X enchancment in MTTD and a 20X enchancment in MTTR. The corporate relies in Silicon Valley. For extra info, go to https://stellarcyber.ai.




















![Lawctopus’ 2 Days Online Workshop on ‘Acquire 8 Skills to Ace Legal Drafting!’ [June 16-17, 7-9 PM]: Register by June 15!](https://i3.wp.com/cdn.lawctopus.com/wp-content/uploads/2024/05/LLS-newtop-1.png?w=120&resize=120,86&ssl=1)
